Correct Answer

verified
Correct Answer
verified
Multiple Choice
Critical Thinking Questions Case 5-1 One form of software theft is the theft of the software from software manufacturers, which is known as piracy. Because this has historically been rather easy to do, the practice has become very common. As a computer instructor you feel it is your responsibility to explain this practice to students through the use of some examples. Which of the following is NOT permissible under a single-user license agreement?
A) Jamie installs Quark Xpress on a single computer.
B) Christine leases her copy of Dreamweaver.
C) Phuong-Dao makes one copy of Microsoft Office 2013 as a backup.
D) Isaiah sells his copy of Adobe Photoshop CS6, having removed it from his computer first.
Correct Answer

verified
Correct Answer
verified
True/False
Combating cybercrime is not one of the FBI's top priorities.
Correct Answer

verified
Correct Answer
verified
True/False
A rootkit can be a back door.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following replaces each character in the plaintext with a different letter by shifting the alphabet a certain number of positions?
A) expansion algorithm
B) Caesar cipher
C) transposition algorithm
D) compaction algorithm
Correct Answer

verified
Correct Answer
verified
Short Answer
A(n) ____________________ control is a security measure that defines who can access a computer, when they can access it, and what actions they can take while accessing the computer.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
COGNITIVE ASSESSMENT Social engineering, as it pertains to computers, is _____________.
A) creating consumer and personal profiles by tracking website history and electronic purchases
B) compiling data from multiple computer users in order to make predictions about computer trends
C) filtering Internet content to targeted users based on their personal preferences
D) gaining unauthorized access or obtaining confidential information by taking advantage of the trusting nature or naivety of users
Correct Answer

verified
Correct Answer
verified
True/False
A digital forensics examiner must have knowledge of the law, technical experience with many types of hardware and software products, superior communication skills, and the like.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
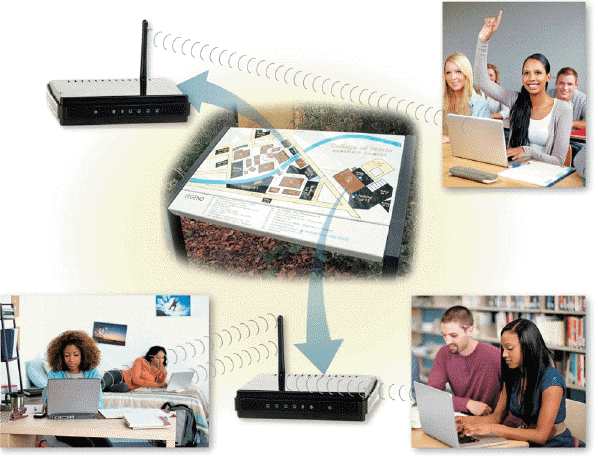 One study found that a certain percentage of wireless connections like the kind in the accompanying figure are unsecured, leaving them susceptible to hackers. What was that percentage?
One study found that a certain percentage of wireless connections like the kind in the accompanying figure are unsecured, leaving them susceptible to hackers. What was that percentage?
A) 25
B) 35
C) 55
D) 75
Correct Answer

verified
Correct Answer
verified
True/False
The Privacy Act forbids federal agencies from allowing information to be used for a reason other than that for which it was collected.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which kind of license is a legal agreement that allows multiple users to access the software on the server simultaneously?
A) site
B) network
C) distributed
D) multipurpose
Correct Answer

verified
Correct Answer
verified
True/False
Content filtering opponents argue that banning any materials violates constitutional guarantees of free speech and personal rights.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is an authorized person or company that issues and verifies digital certificates?
A) certificate authority
B) certificate agency
C) certificate office
D) certificate bureau
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following can transmit germs?
A) iris recognition systems
B) digital forensics systems
C) face recognition systems
D) hand geometry systems
Correct Answer

verified
Correct Answer
verified
Multiple Choice
How long can digital certificates be valid?
A) six months
B) two years
C) four years
D) five years
Correct Answer

verified
Correct Answer
verified
True/False
Passwords and passphrases that are more than four characters, contain uppercase and lowercase letters, numbers, and special characters are the most secure.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
COGNITIVE ASSESSMENT Which term is used to describe software used by cybercriminals?
A) cyberware
B) conware
C) criminalware
D) crimeware
Correct Answer

verified
Correct Answer
verified
Short Answer
____________________ involves the examination of media, programs, data and log files on computers, mobile devices, servers, and networks.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following categories are the rights to which creators are entitled for their work?
A) community property
B) intellectual property
C) creative
D) ethical
Correct Answer

verified
Correct Answer
verified
Multiple Choice
COGNITIVE ASSESSMENT Which of the following terms is used to describe a program that copies itself repeatedly, using up resources and possibly shutting down the computer or network?
A) a virus
B) a worm
C) a Trojan horse
D) a rootkit
Correct Answer

verified
Correct Answer
verified
Showing 101 - 120 of 181
Related Exams