Correct Answer

verified
Correct Answer
verified
Short Answer
Viruses, worms, and Trojan horses all represent malicious software that use _________________________ to find weaknesses or holes in operating systems and networks.
Correct Answer

verified
software e...View Answer
Show Answer
Correct Answer
verified
View Answer
Multiple Choice
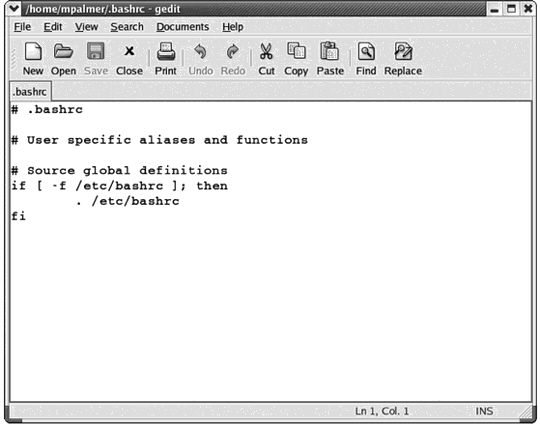 Which of the following operating systems would use the commands listed in the figure above?
Which of the following operating systems would use the commands listed in the figure above?
A) Windows XP
B) Netware 6.x
C) Red Hat Linux
D) Mac OS X
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is notorious for enabling cookie snarfing?
A) SpyNet
B) PeepNet
C) Cookienet
D) Both a and b
E) a, b, and c
Correct Answer

verified
Correct Answer
verified
Essay
What is a benign virus?
Correct Answer

verified
A virus that replicates but does not inf...View Answer
Show Answer
Correct Answer
verified
View Answer
Multiple Choice
How many days of the month does the Code Red worm replicate?
A) 15
B) 19
C) 23
D) 29
Correct Answer

verified
Correct Answer
verified
Essay
List five of the services, applications, systems, or functions that are known to be vulnerable in which attackers may look for problems.
Correct Answer

verified
Any five of the following:
1. DNS servic...View Answer
Show Answer
Correct Answer
verified
1. DNS servic...
View Answer
Essay
What is a destructive virus?
Correct Answer

verified
A virus that is designed to de...View Answer
Show Answer
Correct Answer
verified
View Answer
True/False
Is Sophos Anti-virus free software that can be used in Macintosh, Netware, UNIX/Linux, and Windows-based systems?
Correct Answer

verified
Correct Answer
verified
True/False
Does the AOL4FREE e-mail hoax contain the AOL4FREE.com attachment?
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following executable file extensions is found only on Windows-based systems?
A) .mst
B) .msi
C) .msp
D) .btm
E) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A(n) _____ virus uses defenses to make itself hard to find and detect.
A) polymorphic
B) stealth
C) companion
D) heuristic
Correct Answer

verified
Correct Answer
verified
True/False
Mac OS and NetWare automatically display the boot load information to the screen each time one of these systems is booted.
Correct Answer

verified
Correct Answer
verified
Essay
One way to classify viruses is by how they infect systems. List the four different classifications.
Correct Answer

verified
1. Boot or partition...View Answer
Show Answer
Correct Answer
verified
View Answer
True/False
Backdoor.Egghead is an example of a worm that is spread by buffer overflows.
Correct Answer

verified
Correct Answer
verified
True/False
The Windows 2003 Server ASR set backs up all system files, system settings, and application data files.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is an example of a Red Hat Linux file that can be the target of a virus?
A) autoexec.bat
B) inittab
C) startup.ncf
D) win.ini
Correct Answer

verified
Correct Answer
verified
Multiple Choice
How was the Melissa virus transported?
A) File sharing
B) Floppy disk
C) Buffer overflow
D) E-mail
Correct Answer

verified
Correct Answer
verified
True/False
A(n) macro virus, worm, or Trojan horse is a file that contains lines of computer code that can be run.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
_____ is designed so that it does not infect all of these file types at once, but only a limited number each time Windows Explorer runs.
A) INIT 1984
B) Code Red
C) Slammer worm
D) W32.Pinfi
Correct Answer

verified
Correct Answer
verified
Showing 21 - 40 of 86
Related Exams