A) 172.16.1.80
B) 172.16.2.80
C) 172.16.1.64
D) 172.16.2.64
E) 172.16.2.127
F) 172.16.2.128
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Exhibit: 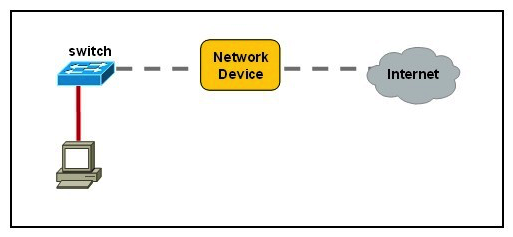 Refer to the exhibit. An industrial ruggedized network device needs to be installed in the place of the icon labeled Network Device to accommodate a leased line attachment to the Internet. Which network device and interface configuration meets the minimum requirements for this installation?
Refer to the exhibit. An industrial ruggedized network device needs to be installed in the place of the icon labeled Network Device to accommodate a leased line attachment to the Internet. Which network device and interface configuration meets the minimum requirements for this installation?
A) a router with two Ethernet interfaces
B) a switch with two Ethernet interfaces
C) a router with one Ethernet and one serial interface
D) a switch with one Ethernet and one serial interface
E) a router with one Ethernet and one modem interface
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Why is SSH preferred over Telnet as a method of accessing a network device to alter or view the configuration?
A) Telnet encrypts only the login information, not the entire transmission.
B) SSH requires fewer network resources and no additional configuration.
C) Telnet is more difficult to use and configure than SSH.
D) SSH encrypts the login and session information.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What are two recommended tools or commands that allow you to troubleshoot connectivity between two devices in different IP networks? (Choose two.)
A) show interface status
B) show spanning-tree
C) ping
D) show interfaces gigabitEthernet x/y switchport
E) traceroute
F) show interface
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which prompt is used to configure parameters for the Ethernet ports of an industrial switch?
A) Switch(config-if) #
B) Switch(config-if-ind) #
C) Switch(config-line) #
D) Switch(config-ind) #
E) Switch(config-vlan) #
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which option best describes a mechanical, ingress, climatic, chemical and electromagnetic environment that is classified as M3 I3 C3 E3?
A) the highest quality
B) office environment
C) severe
D) serviced by multiple cable segments
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Given a ring topology, which loop prevention mechanism provides the fastest reconvergence time after a link failure?
A) Rapid Per-VLAN Spanning Tree Protocol
B) Resilient Ethernet Protocol
C) Multiple Spanning Tree Protocol
D) Spanning Tree Protocol
Correct Answer

verified
Correct Answer
verified
Multiple Choice
EtherNet/IP is an Ethernet implementation of which protocol?
A) CIP
B) Industrial Protocol
C) DeviceNet
D) ControlNet
Correct Answer

verified
A
Correct Answer
verified
Multiple Choice
What are the two most relevant factors in determining the class of administration that is required to maintain the telecommunications infrastructure? (Choose two.)
A) the size of the infrastructure
B) the complexity of the infrastructure
C) the age of the infrastructure
D) the industry that the infrastructure supports
E) the physical environment of the infrastructure
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is the purpose of Spanning Tree Protocol?
A) to prevent routing loops
B) to create a default route
C) to provide multiple gateways for hosts
D) to maintain a loop-free Layer 2 network topology
E) to enhance the functions of SNMP
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which three of the following components must be elected before the Spanning Tree Protocol can converge in a switched LAN? (Choose three.)
A) designated ports
B) duplex operating mode
C) fast mode ports
D) root bridge
E) root ports
F) BDPU priority
Correct Answer

verified
A,D,E
Correct Answer
verified
Multiple Choice
What are two symptoms of duplex mismatch? (Choose two.)
A) Ping does not return from one direction versus the other direction.
B) Communication is slow and locks up.
C) Speed is seen equally slow in both directions.
D) The half-duplex side sees frame sequence errors or runt frames.
E) The full-duplex side sees CRC errors.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which characteristic causes multimode fiber-optic cable to differ from single mode?
A) by allowing multiple network services in the same cable
B) shorter maximum network segment length for a given bandwidth
C) a wider variety of available connector types
D) use outdoors as well as indoors
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following correctly pairs the dotted decimal subnet mask with the correct number of binary bits that represent the subnet mask?
A) 255.255.255.192 and /25
B) 255.255.255.248 and /28
C) 255.255.255.224 and /26
D) 255.255.255.248 and /27
E) 255.255.255.240 and /28
F) 255.255.255.240 and /16
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What are two benefits of a star network topology? (Choose two.)
A) Disruption of the entire network is not required when adding new machines.
B) Any problem which leaves the network inoperable can be traced to the central hub.
C) This network type requires less cable as compared to linear bus topology.
D) The performance of one of the numerous nodes cannot reflect on the performance of other nodes.
E) The performance of the entire network is directly dependent on the performance of the hub.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
For which three issues should fiber-optic network segments be tested? (Choose three.)
A) attenuation
B) near-end crosstalk
C) length
D) polarity
E) jitter
F) tensile stress
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Exhibit: 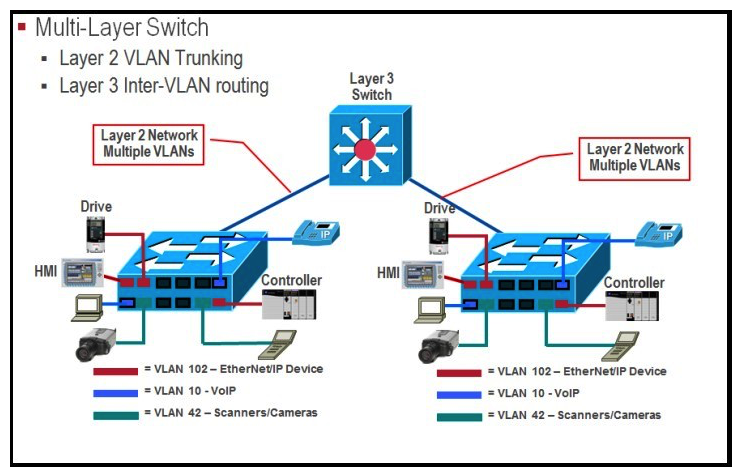 Refer to the exhibit. What are three traffic and interconnection requirements for the devices in the exhibit? (Choose three.)
Refer to the exhibit. What are three traffic and interconnection requirements for the devices in the exhibit? (Choose three.)
A) The EtherNet/IP drive connections are in a high-voltage area and need protection from electromagnetic noise, so shielded cable that is rated for 600 V is advised.
B) EtherNet/IP devices such as the controller, drive, VoIP phone, and IP camera should be in the same VLAN.
C) CIP traffic has the highest bandwidth requirement so it needs the highest QoS setting.
D) EtherNet/IP drive traffic has high sensitivity to random drops, latency, and jitter.
E) Real-time motion control and VoIP traffic can share the same VLAN with the proper QoS setting.
F) IEEE1588 and PTP are important for ensuring real-time synchronization.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A small manufacturing company has a Class C network address on the plant floor and needs to create five subnets, each accommodating 25 endpoints. Which subnet mask needs to be configured?
A) 255.255.240.0
B) 255.255.255.128
C) 255.255.255.192
D) 255.255.255.224
E) 255.255.255.240
F) 255.255.255.248
Correct Answer

verified
D
Correct Answer
verified
Multiple Choice
Which two ports does EtherNet/IP use to communicate? (Choose two.)
A) TCP 44818
B) UDP 44818
C) TCP 502
D) UDP 502
E) TCP 2222
F) UDP 2222
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What should be done with unused conductors in copper unshielded or shielded twisted-pair network cables?
A) terminate in their characteristic impedance
B) trim back and properly insulate
C) connect to protective earth
D) splice to a used conductor
Correct Answer

verified
Correct Answer
verified
Showing 1 - 20 of 36
Related Exams