A) route summarization
B) stub area
C) route filtering
D) not-so-stubby area
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An IBGP mesh design is being scoped, and in the discussions, one of the design engineers proposes the use of route reflectors. Which limitation is valid when using route reflectors in this design?
A) The configuration complexity on the routers will be increased.
B) Route reflectors will limit the total number of routes in the topology.
C) Multipath information is difficult to propagate in a route reflector topology.
D) Route reflectors will cause an opportunity to create routing loops.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
During a network design review, it is recommended that the network with a single large area should be broken up into a backbone and multiple nonbackbone areas. There are differing opinions on how many ABRs are needed for each area for redundancy. What would be the impact of having additional ABRs per area?
A) There is no impact to increasing the number of ABRs.
B) The SPF calculations are more complex.
C) The number of externals and network summaries are increased.
D) The size of the FIB is increased.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
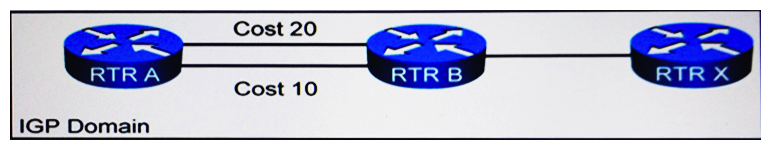 Refer to the exhibit. Router A must reach Router X. Which option describes how router A decides which interface to use to forward packets?
Refer to the exhibit. Router A must reach Router X. Which option describes how router A decides which interface to use to forward packets?
A) Router A does per-flow load-balance across the two interfaces.
B) Router A relies on RIB toselect the desired interface.
C) Router A relies on FIBto select the desired interface.
D) Router A does per-packet load-balance across the two interfaces.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
VPLS is implemented in a Layer 2 network with 2000 VLANs. What is the primary concern to ensure successful deployment of VPLS?
A) VLAN scalability
B) PE scalability
C) The underlying transport mechanism
D) Flooding is necessary to propagate MAC address reachability information
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which two benefits are of protecting the control plane of a network device? (Choose two.)
A) protects against DoS attacks targeted at the network infrastructure
B) increases the reliability, security, and availability of the network
C) protects data flowing through devices
D) separates attack traffic from normal network traffic
Correct Answer

verified
Correct Answer
verified
Multiple Choice
When designing a network, which method can be used to control the exit point for traffic leaving an autonomous system, at the Layer 3 control plane?
A) tuning the metric of the underlying IGP
B) tuning the multi-exit discriminator
C) setting the Site of Origin extended community
D) prepending AS path
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which description is true about downstream suppression?
A) the ability of a fault management tool to generate alerts for only an upstream device failure and to suppress the alarms related to all unreachable downstream sites
B) the ability of a router to suppress downstream route fluctuations to avoid introducing instability into the network core
C) the ability of a network management station to perform root cause analysis on a network fault and remove duplicates of all other alarms resulting from fault symptoms
D) the ability of an element manager to restrict forwarding to critical performance alarms northbound to the Manager of Managers and suppress other alarms
Correct Answer

verified
Correct Answer
verified
Multiple Choice
EIGRP performs route summarization at the interface level with the ip summary-address command. Which three statements correctly describe EIGRP route summarization? (Choose three.)
A) Summary routes are inserted in the routing table with a next hop of null 0 and a high administrative distance, to prevent black holing of traffic.
B) By default, EIGRP automatically summarizes internal routes, but only each time a major network boundary is crossed.
C) EIGRP route summarization can reduce the query diameter to help prevent SIA problems.
D) The metric for each summarized route is inherited from the lowest metric of the component routes.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which two OSPF design considerations should you implement to support the eventual growth of a network, so that CPU and memory are unaffected by the size and complexity of the link-state database in a large service provider network? (Choose two.)
A) Turn on route dampening.
B) Create network summaries.
C) Turn on the Incremental SPF feature.
D) Add more memory.
E) Turn on packet pacing.
F) Add redundancy between critical locations.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A switched network is being deployed on a factory floor. Due to cost constraints, fiber-based connectivity is not an option. Which design allows for a stable network when there is a risk of interference from the manufacturing hardware in use on the factory floor?
A) Design the network to include loop guard to prevent a loop in the switched network when a link has too much interference
B) Design the network to include backbone fast on all devices to accelerate failure convergence times
C) Design the network to include UDLD to detect unidirectional links and take them out of service
D) Design the network to include EtherChannel bundles to prevent a single-link failure from taking down a switch interconnection point
Correct Answer

verified
Correct Answer
verified
Multiple Choice
In a redesign of a multiple-area network, it is recommended that summarization is to be implemented. For redundancy requirements, summarization is done at multiple locations for each summary. Some customers now complain of higher latency and performance issues for a server hosted in the summarized area. What design issues should be considered when creating the summarization?
A) Summarization adds CPU overhead on the routers sourcing the summarized advertisement.
B) Summarization prevents the visibility of the metric to the component subnets.
C) Summarization creates routing loops.
D) Summarization causes packet loss when RPF is enabled.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which mechanism should be added to a network design to identify unidirectional Spanning Tree Protocol failures through BPDU loss?
A) UDLD
B) loop guard
C) BPDU guard?
D) root guard
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Acme Corporation wants to minimize the risk of users plugging unauthorized switches and hubs into the network. Which two features can be used on the LAN access ports to support this design requirement? (Choose two.)
A) BPDU Guard
B) PortFast
C) Loop Guard
D) Port Security
E) UDLD
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A virtual storage area network (VSAN) is a collection of ports from a set of connected Fibre Channel switches, that form a virtual fabric. Which technology allows centralized storage services to be shared across different VSANs?
A) IVR
B) FSPF
C) FICON
D) SANTap
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which three network management requirements are common practices in a network design? (Choose three.)
A) Ensure that all network devices have their clocks synchronized
B) Look at inconsistent and bursty KPIs such as CPU utilization and interface utilization
C) Collect RMON poll information for future regression analysis
D) Validate data plane health, application, and services availability with synthetic traffic
E) Capture ingress and egress flow-based packets, while avoiding duplication of flows
F) Collect SNMP poll information for future regression analysis
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which description is true about RSVP reservations?
A) static, and cannot be removed once they are first requested by a delay-sensitive, real-time application
B) static, and must always be installed after power-up
C) dynamic, and depend on the amount of delay-sensitive, real-time data passing through
D) dynamic, allocated when requested, and removed at the end of each session for which they were requested
Correct Answer

verified
Correct Answer
verified
Multiple Choice
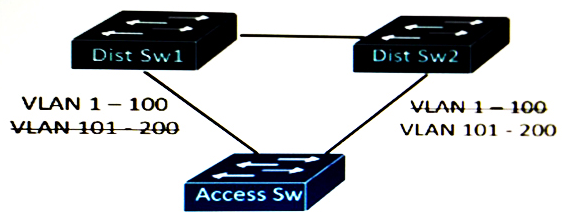 Refer to the exhibit. This Layer 2 network is expected to add 150 VLANs over the next year, in addition to the existing 50 VLANs within the network. Which STP type will support this design requirement using the least amount of CPU resources and achieving load-balancing?
Refer to the exhibit. This Layer 2 network is expected to add 150 VLANs over the next year, in addition to the existing 50 VLANs within the network. Which STP type will support this design requirement using the least amount of CPU resources and achieving load-balancing?
A) MST
B) CST
C) PVST+
D) RSTP
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which VPN management feature would be considered to ensure that the network had the least disruption of service when making topology changes?
A) dynamic reconfiguration
B) path MTU discovery
C) auto setup
D) remote management
Correct Answer

verified
Correct Answer
verified
Multiple Choice
In a network design using carrier Ethernet, which three mechanisms can be used to improve Layer 2 down detection and thereby reduce routing convergence time? (Choose three.)
A) BFD
B) Ethernet port debounce timers
C) link-state tracking
D) object tracking
E) fast IGP hello
Correct Answer

verified
Correct Answer
verified
Showing 561 - 580 of 660
Related Exams