A) Relying on a single sign-on based password manager
B) Enabling automatic full disk encryption to protect data with no productivity sacrifice
C) Automated data and file backups
D) Deploying all VPN connections in the transport mode
E) Using passphrases rather than passwords
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The defense-in-depth principle may include security measures of the following layers. Which layer is LEAST relevant?
A) Application security
B) External network security
C) Host security
D) Internal network security
E) Perimeter security
Correct Answer

verified
Correct Answer
verified
Multiple Choice
In realizing the defense-in-depth principle, the perimeter security technologies of a business organization include the following EXCEPT:
A) Border firewalls
B) Corporate file access control
C) Access Control List (ACL) on border routers
D) Demilitarized zone (DMZ)
E) Proxy servers
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which CORRECTLY pairs a security layer and an available technology in realizing the defense-in-depth principle?
A) Data security -- Access Control List (ACL) on border routers
B) Application security -- Hardening intermediary devices
C) Host security -- Anti-virus protection
D) Internal network security -- Corporate-wide data encryption
E) Perimeter security -- Network segmentation (e.g., subnets, VLANs)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Maintaining data privacy achieves the _________ aspect of security requirement.
A) confidentiality
B) integrity
C) authentication
D) access control
E) reliability
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is NOT a technology solution intended for authentication?
A) Password and passphrase
B) Access control list (ACL)
C) Digital signature and digital certificate
D) Biometric solutions (e.g., fingerprints) .
E) Security token
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which is NOT a primary security requirement?
A) confidentiality (privacy)
B) data integrity
C) authentication
D) access control
E) spoofing detection
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Below email is an example of _________: 
A) sniffing
B) spoofing
C) monitoring
D) phishing
E) scanning
Correct Answer

verified
D
Correct Answer
verified
Multiple Choice
_____ is a process that validates "you are the person/system you claim to be."
A) Address filtering
B) Challenging
C) Certification
D) Authentication
E) Authorization
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Maintaining a reliable backup system of corporate database satisfies what aspect of security requirements?
A) Confidentiality
B) Data integrity
C) Authentication
D) Authorization
E) Availability
Correct Answer

verified
E
Correct Answer
verified
Multiple Choice
The following figure demonstrates the ________ principle in security. 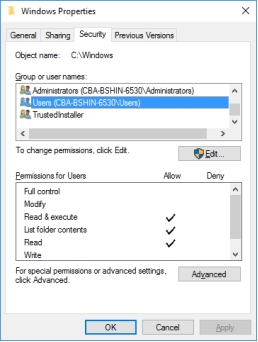
A) Limiting
B) Simplicity
C) Layering
D) Defense-in-depth
E) Hiding
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The following elements/activities cut across all security layers in realizing defense-in-depth EXCEPT:
A) Corporate-wide data encryption
B) Regulatory compliance self-assessment
C) Security policies & procedures
D) Security awareness & training
E) Information security self-assessment
Correct Answer

verified
A
Correct Answer
verified
Multiple Choice
The following figure is an example of ___________ attack. 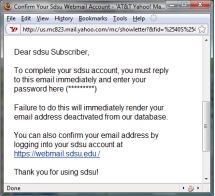
A) social engineering
B) denial of service
C) malware
D) fingerprinting
E) man-in-the-middle
Correct Answer

verified
Correct Answer
verified
Showing 1 - 13 of 13
Related Exams